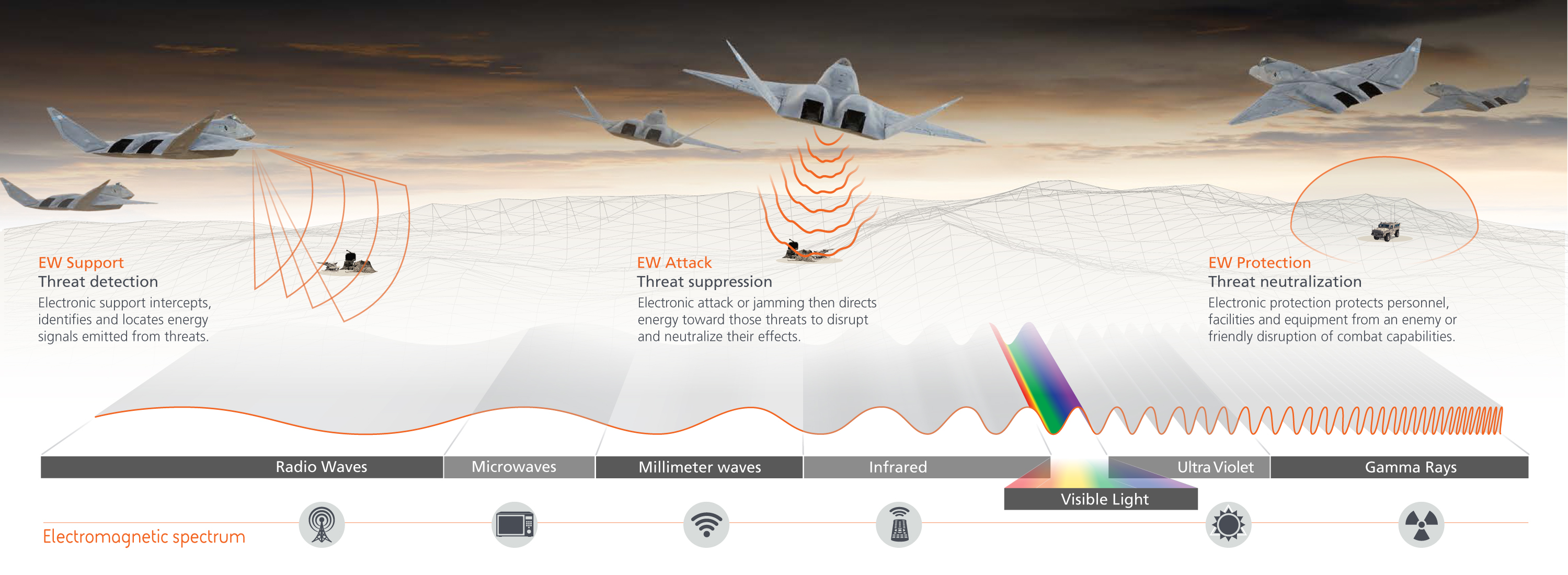
//This is my original text before editing//
European newspapers have shared a German assessment of what a Russian assault on NATO and the Baltics could look like. If you want to understand your adversary, put yourself in his shoes, and so I did. I decided I would start war planning for the assault immediately. The Kremlin loves a mighty name on a war plan, like the Americans who spend a lot of energy and time to come up with the most appealing name for an operation, even the later failed ones, so I spun on the old Soviet plan “Seven days to the Rhine.” My plan: “Plan Red – Three Days to Paldiski” – was a success as soon as the Leningrad MD heard about it.
When I started to write the plan, I needed to list the assumptions that laid the foundation for the plan.
My five grander general assumptions are straightforward.
First, most Western European Armed Forces are in a grave state of dismantled readiness and have limited abilities. Even significant forces such as Germany, France, and Great Britain might talk big and politically market their rearmament programs, but at the actual units, the readiness is still as it was ten years ago. The first significant NATO formation that arrived at the Lithuanian border would be Polish after three days, which was the cut-off for the plan, but the German and other European NATO forces would not be seen for at least ten to fifteen days. The Western European NATO members are in a state of denial of their readiness, living in an imaginary world where the recent years’ talk of rearmament is already in place. One example is Gotland, which is still only defended by two mechanized companies and some Home Guard. The difference between imagined readiness and actual readiness forms our opportunity.
Second, since the Cold War, the fear of nuclear arms in Western Europe has built up to the degree that the political debate does not even talk about these weapons anymore. At least in the 1970s and 1980s, there was a discussion. Added to the silence about nuclear arms is the almost eighty-year-old geopolitical equilibrium where nuclear arms are not used and are seen as theatrical instruments to portray strategic deterrence. If we, the Russians, use nuclear arms it would send shock waves not only through the political and military leadership and systems, but also create chaos on the financial market at a global scale. The attack on the World Trade Center at 9-11 was not only a deadly event, it created total mayhem on the global stock markets, and pushed the US into recession. It might not be nice, but it serves the Russian interest well.
Third, I assess that any NATO “trip wire” units in the Baltics will be passive. These units do not have artillery, logistics, medical support, or heavy weapons to engage a Russian spearhead. So if we, the Russian army, circumvent these NATO units, there will be no interference during our operational windows during the first three days. The “trip wire” units will not attack but hold the territory where they are stationed, and we will drive around it. Finland will not have time to mobilize or push units towards Russia, nor will Finland cross over the Russian border, fully aware of the risk of a nuclear response. Russia does not need to dedicate units beyond the regular staffing along the Finnish border.
Fourth, we are better off with a smaller force and no sign on the surface of what we are up to than large troop movements, hybrid warfare, loud propaganda, and psychological operations. These actions will only alert NATO. We can achieve the same goal with a regiment that needs a division if NATO starts to understand our intentions. We will not share our intentions with the government or foreign entities; even China will be unaware. In the assault on Ukraine, there was almost no surprise; we ran into massive resistance early.
Fifth, We, the Russians, will create a false illusion that there is a political solution, a settlement and that we are open to realizing that peace is better than conflict. The default belief in a political, diplomatic solution will slow the Western response, and create political division and indecisiveness in critical junctures. From the first armored column that passes the Estonian border, we will use all diplomatic channels to send this message of confusion and delay – that there is a political, diplomatic solution. The numerous governments that form NATO will lose valuable time discussing a diplomatic solution that never existed – but it serves our Russian objectives.
The actual plan is simple.
PLAN RED: THREE DAYS TO PALDISKI
Day one, a missile barrage on high-value targets opens up the engagement. One echelon of armor, attack helicopters, and rocket artillery supported by rocket artillery push through the Northern Estonia – Narva, Reval (Tallinn) to Paldiski. Batallion-size naval infantry land in Reval (Tallinn) harbor simultaneously.
In the South, another echelon pushes to Kaliningrad Oblast through Lithuania and immediately turns South to defend against NATO troops coming from Poland. Rear forces mop up the Lithuanian defenses and resistance in the days to come.
Latvia is ignored and sits in a Kurland Kessel, the Courland pocket, and the Latvian army does not have the means to attack in any direction.
A high-altitude nuclear EMP weapon detonated on international waters knock out installations on Gotland, including Visby airport, and a battalion-sized airborne unit captures Visby airfield. Day two, secure the targets for day one and reinforce the echelons.
When the Polish army arrives day three, direct communication with NATO declaring that any attempt to occupy the Baltic oblasts will have a nuclear response followed by a demonstration of a massive nuclear attack by the Strategic Rocket Forces on the Russian borderland in Novaya Zemlya, the large island North of Murmansk, and in the East Siberian Sea in the Far East.
Then a Kremlin phone call to NATO leadership – what are you gonna do about it?
The peace deal is that Russian forces leave Gotland. That’s it.
Jan Kallberg, Ph.D., LL.M., is a non-resident Senior Fellow with the Transatlantic Defense and Security program at the Center for European Policy Analysis (CEPA) and a George Washington University faculty member. Follow him at cyberdefense.com and @Cyberdefensecom.